Archethic Blockchain & Uniris Identity Solution Tech Overview
The Archethic Blockchain Designed for global use
A Truly Decentralized and Unlimited Network
Given the universal constraints both material and physical, billions of transactions cannot be integrated into a single branch of chained blocks. Similarly, regardless of the consensus method, it is not possible to ensure universal consensus on billions of transactions by polling all nodes of the network. Finally, the functioning of current distributed networks (P2P) is such that it is not possible to guarantee the freshness (consistency) of data on an asynchronous network, unless the network is slowed down excessively by the calculation of the nonce of the block (PoW), as is the case with the Bitcoin network. Archethic solved these problems in the following ways:
Infinite Chains of Transactions vs a chain of blocks

Instead of chained blocks of transactions, each block is reduced to its atomic form, i.e. each block contains one transaction and each transaction will be chained in its own chain.
ARCH Consensus: the absolute consensus
ARCH or “Atomic Rotating Commitment Heuristic (ARCH)” is a new generation of Consensus. Following is a detailed explanation of each concept of ARCH:
- Atomic Commitment is the form of “absolute” consensus that implies 100% concordant and positive responses or the refusal of the validation of transaction.
- Heuristics is the set of algorithms, software and parameters that manage the entire network, allowing the network to elect in a decentralized and coordinated way, the nodes in charge of validating and storing transactions chains.
- Rotating, the network being fully distributed (no central or privileged role), the nodes elected for each operation are constantly changing so that no node can predict which node will be elected until the transaction arrives.
Predictive, Optimized, Geo-secure Replication System capable of self-repair
Instead of synchronizing transactions in a disorganized way across the entire network, each transaction chain will be stored in a reproducible and ordered way on a set of nodes — thus each node, independently, will know all the nodes hosting a given transaction and will thus be able to relieve the network by interrogating only the closest “elected” nodes. The election of storage nodes also includes the geographical position to ensure data security even in the event of disaster in one or more geographical areas.
Distributed Network (P2P) without saturation point
Based on Supervised Multicasting, the peer-to-peer network uses a self-discovery mechanism based on incoming connections and the network transaction chain mechanism to maintain a qualified and trusted vision while generating a minimum of new transactions on the network.
Beacon Chains
Since no node has the physical ability to know the status of each transaction in an unlimited network, the Archethic network uses a set of specific transaction chains, each containing a subset of the addresses of the last transactions for a given date, allowing any node to automatically resynchronize itself in the event of disconnection.
Oracle Chains
The “State of the World” Oracle chains are updated by consensus every time information is updated (for example, when a new weather report is broadcast, news …).
Prediction Module
To enable a decentralized network to survive decades or even centuries, it must be able to adapt to threats and react accordingly. For this purpose, the Archethic network has a prediction module capable of linking a network disturbance (e.g. unavailability of nodes in a geographical area) to an event (e.g. storm in that area via Oracle).
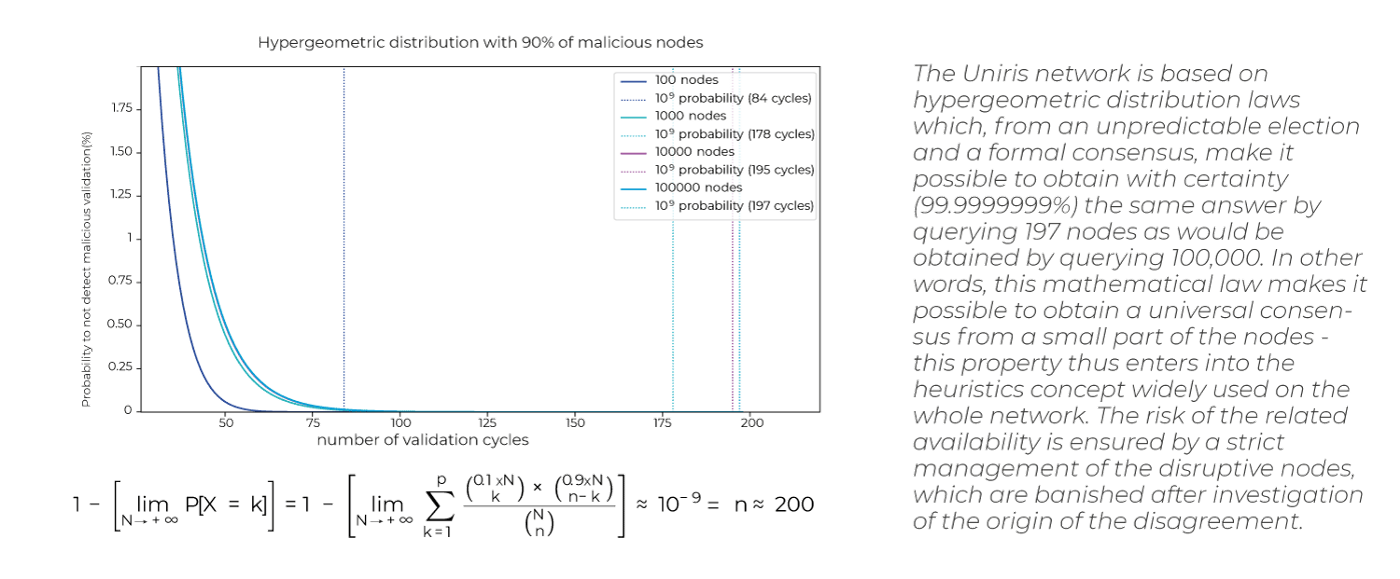
Mining, Proof of Work & Energy Consumption
The election of nodes and network synchronization being ensured by the Heuristic algorithms, proof of work is used to check that the nodes causing the validation and the device causing the transaction are authorized (e.g. biometric device) allowing authentication to be completed by its context (e.g. electronic voting requiring the real identity of a voter). Since the random election of nodes is no longer linked to energy expenditure, network energy consumption is reduced by 3.6 billion times compared to the Bitcoin network.
All that elements are explained in a detailed way inside Yellow Paper.
Smart-Contracts designed to improve any application or service
First created by the Bitcoin network for updating a shared ledger, then enhanced by the possibility to perform programmed actions through smart contracts up to the ability to completely operate systems, Blockchain technology continues to reinvent itself. Unlike smart-contracts compiled on Ethereum, the smart-contracts on the Archethic network are directly interpreted and atomically validated by the miners. Every transaction or smart-contract is stored on a specific group of nodes (rotating heuristic election : ARCH) that can then synchronously load a set of new features: for example, to know the status of the stock, the number of votes and the transactions in the same smart-contract (any transaction to a smart-contract is notified and stored on the group of nodes) or automatically trigger an action on the arrival of an event (date, weather, etc.) thereby supporting any real use-case.
To ensure security and irrevocability of smart-contracts, these are entirely based on the UTXO model (release of unspent transaction) that can be spent/used as an entry into a new transaction. In other words, smart-contracts are not dependent on the state of an internal database but only on the transactions already validated.
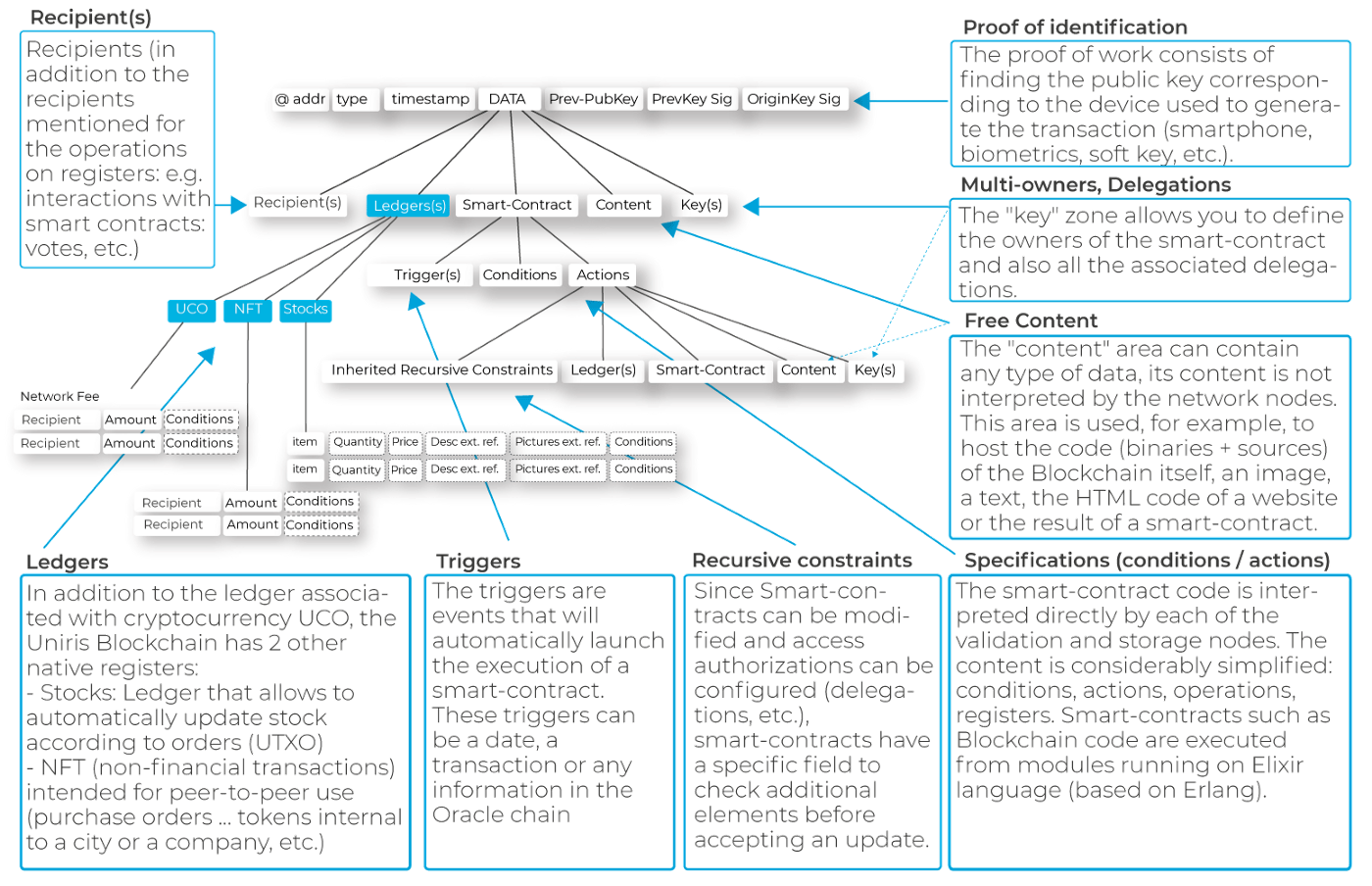
Whether it’s a simple transfer, a rule of access to a building, an online store, hosting a website, a country-wide vote or even all the code used on the network itself, any transaction follows the following pattern:
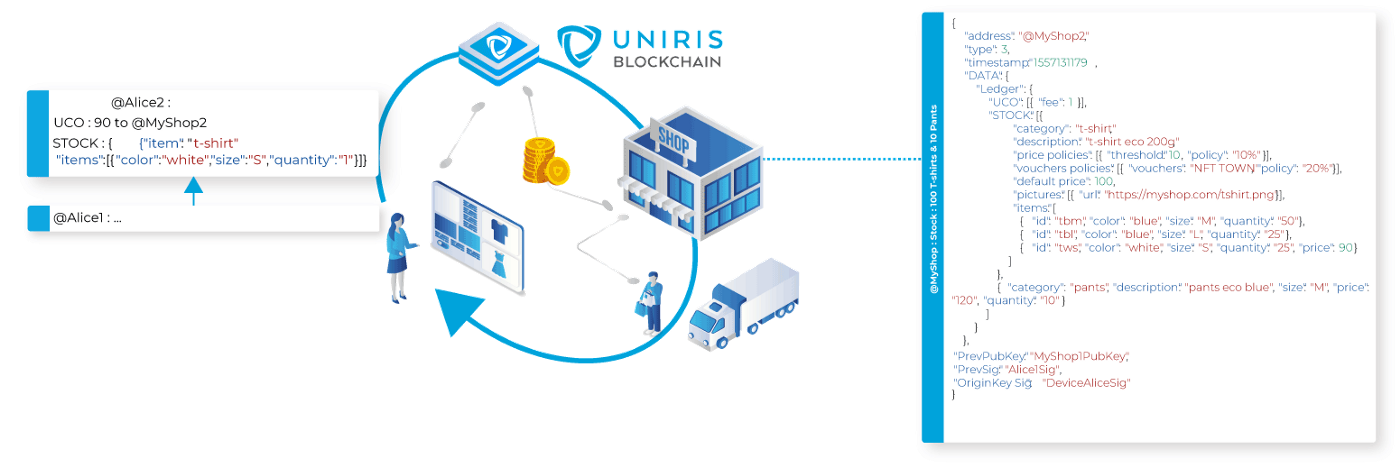
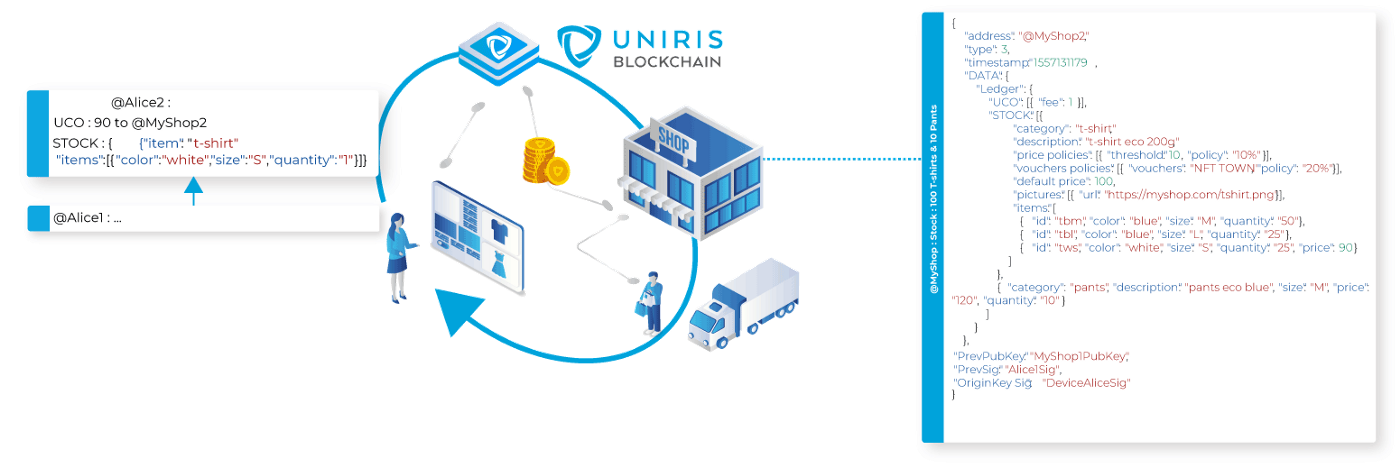
Smart-contract example for a marketplace
In the UTXO model, the only references are the validated transactions, for example, for a merchant site the stock status is not changed in the smart contract itself, but is reconstructed from the validated transactions. The experience of a user or a merchant is absolutely identical since each state is irrefutable and unambiguous.
Decentralized Identity and Biometrics : The Grail of Mass Adoption
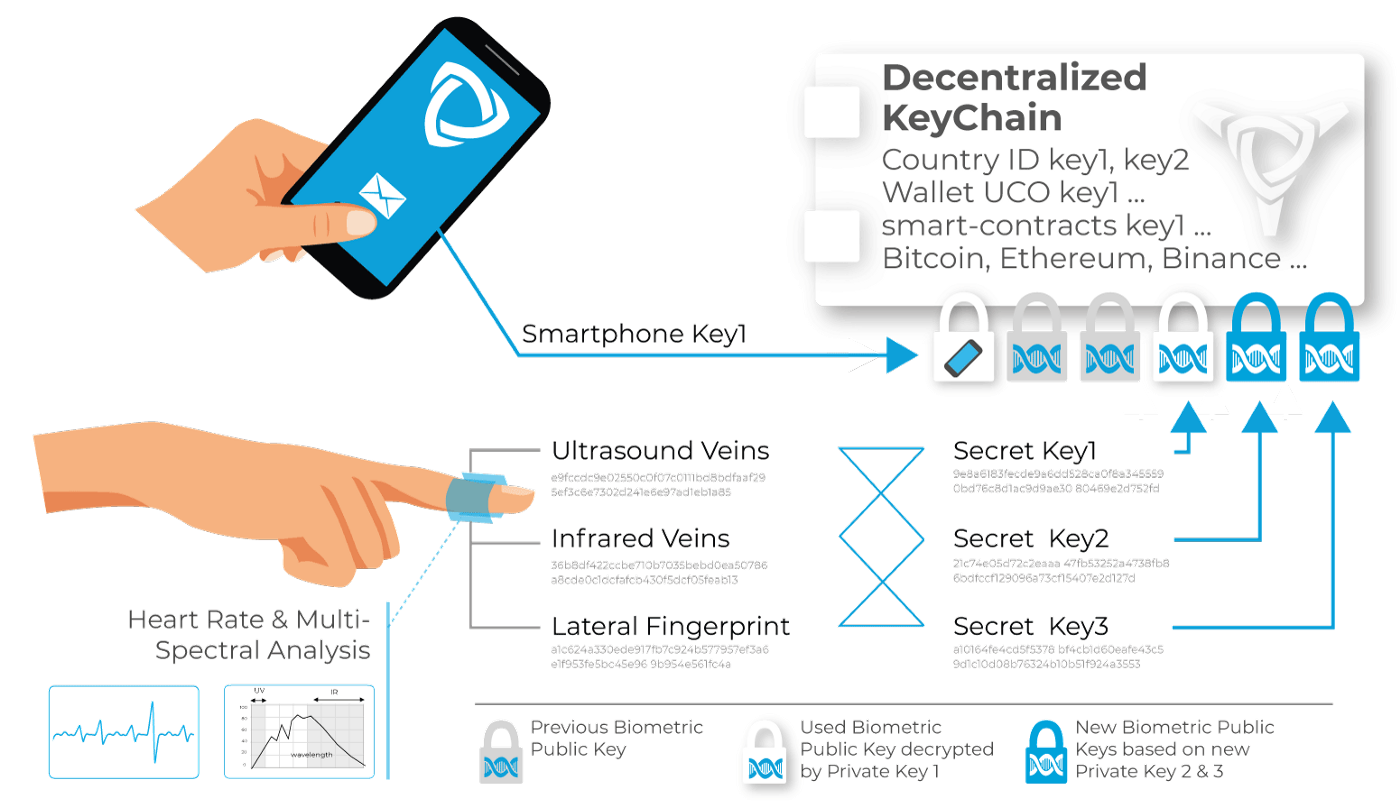
No one will be able to steal your keys, you will be able to delete them, but you will never forget or lose them.
Tamper-proof authentication
No key storage (GDPR by design)
Vital signs monitoring
Learning morphological changes
Designed for the world’s population
An authentication that cannot be used without our knowledge
Unlike fingerprints, irises, faces that can easily be reproduced and falsified from a photo on Facebook or in the street — it is impossible to reconstruct the inside of a finger. The device checks vital signs during each authentication to ensure that the finger has not been cut off and that the person is fully aware and consenting, before any transaction validation.
Without key storage
All current biometric identification are based on the same principle:
- capture of biometric data and storage of that recognition data (pattern)
- comparison of the measurement with the pattern
- if the match exceeds a certain threshold then the person is identified (software)
Identification by the Uniris biometric device is no longer based on a recognition threshold and therefore no longer needs to be stored for comparison.
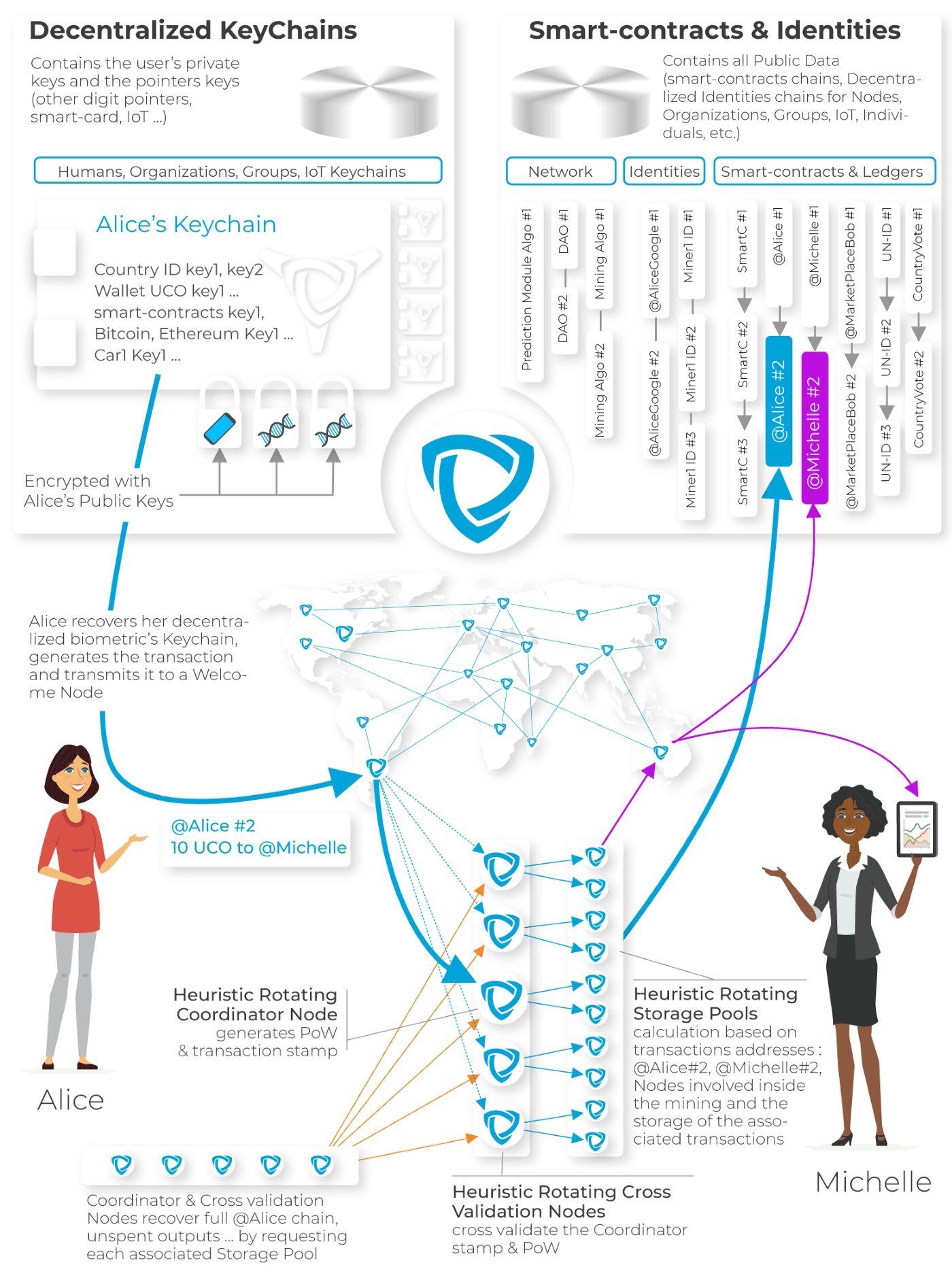
As shown in the figure opposite, private cryptographic keys are generated on the fly (and then deleted), allowing the user to retrieve and decrypt their decentralized “key ring”. Tolerance on identification is ensured by the learning mechanism described above. Finally, authentication is no longer software, but cryptographic, making any attempt of software attack useless.
An authentication of the world population independent of the system
Unlike biometric identification on a smartphone that will only work on one smartphone — Uniris authentication works for any person and on any device. As no keys are stored, it is compatible with the most stringent data protection regulations (GDPR, CNIL, etc.), making biometrics available for large-scale use.
Automatic lifelong learning
As shown in the figure above, the keys are generated in pairs from the biometric measurements. If one of the measurements is different (cut, burn, etc.) then only one key will match and can validate the authentication while the two new keys will be added to encrypt (via associated public keys) the decentralized key ring, thus learning a person’s new biometric measurements without ever having to store the keys.
Proof of the origin of the authentication via Proof-of-work
Identification on the Archethic network is not limited to biometric devices(by Uniris) and as shown in the figure above, each access method (smartphone, USB key, software key, etc.) will have its own certification method (see Yellow Paper Season 1). The identification method being associated with the transaction (see smart-contract schema: “OriginKey Sig”) and the proof-of-work, will thus allow adjustment of the required security with any smart-contract or portfolio — for example:
- A transaction of less than 1000 UCO can be carried out from a specific smartphone but only from a biometric device beyond that value.
- Entry into a sensitive building may be made by NFC during the office hours and biometrics outside those hours.
Decentralized and Interoperable Identity
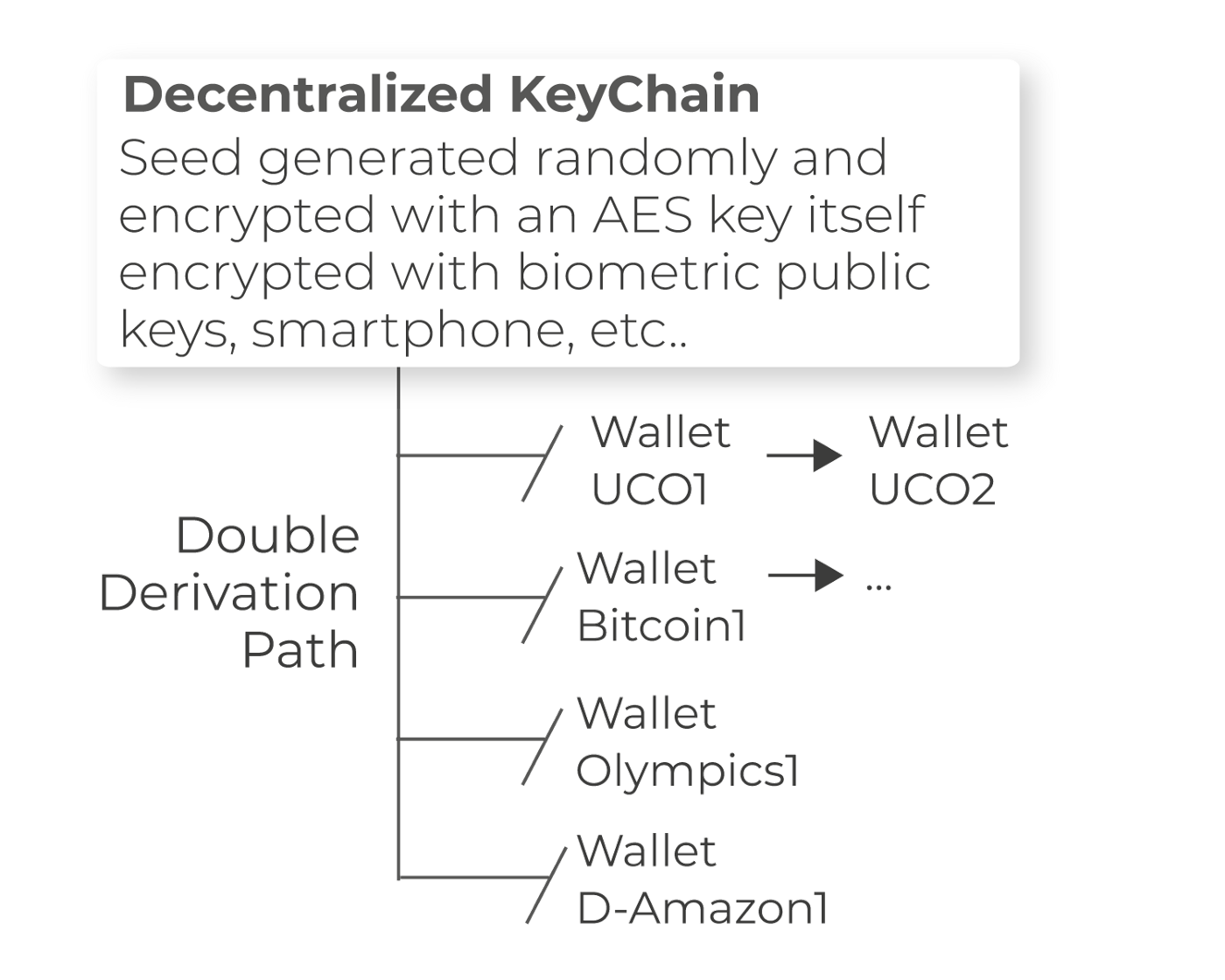
Technically, the decentralized identity of a person or a connected object is made up of randomly generated Seed (root key) from which it is possible to generate all keys according to a path of derivation. So for any access to a service or an application, a key will be calculated on the fly from the seed (root key) and the first public key associated with a service or an application. Thus allowing to create an infinite number of identities without even having to store related keys. All features associated with this decentralized identity will be detailed in the Yellow Paper Season 4: Automated address books, email, FIDO2.
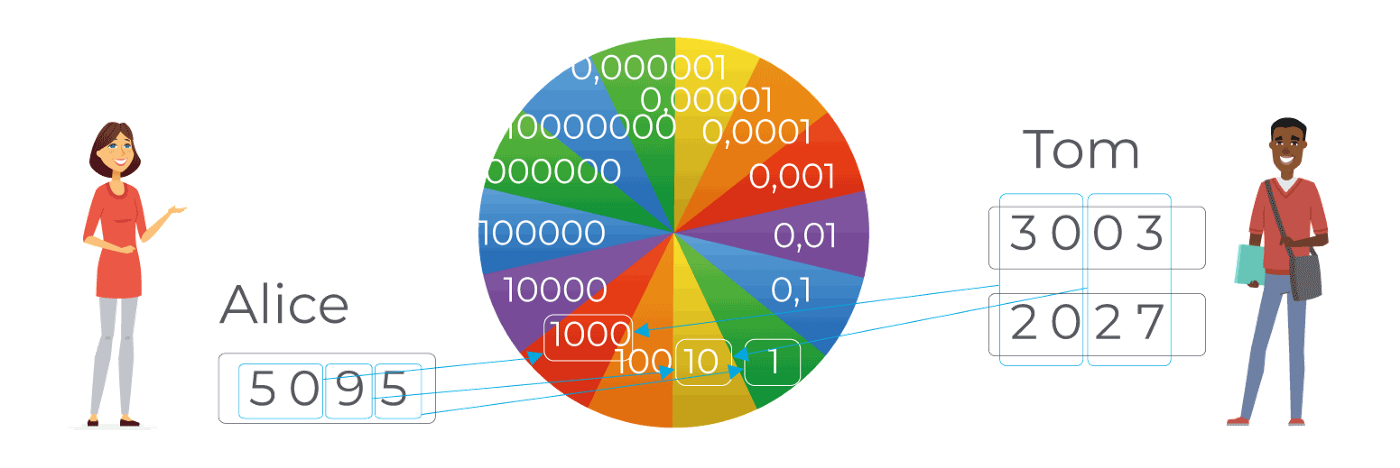
Wheel of privacy
As all transactions are public, the network has a mechanism called the “Wheel of Privacy” to remove correlations between the sender, the recipient, the time and the amount of transaction. This mechanism is used in particular for electronic voting and allows everyone to keep their vote private without compromising the consistency of the vote logs.
Big Picture : An example of cryptocurrency transfer
Mind Map
Archethic Public Blockchain
Archethic is a Layer 1 aiming to create a new Decentralized Internet.
Its blockchain infrastructure is the most scalable, secure & energy-efficient solution on the market thanks to the implementation of a new consensus: "ARCH".
Archethic smart contracts expand developers' boundaries by introducing internal oracle, time-triggers, editable content & interpreted language.
Through native integration for DeFi, NFTs & decentralized identity; Archethic offers an inclusive and interoperable ecosystem for all blockchains.
In order to achieve the long-term vision of an autonomous network in the hands of the world population, we developed a biometric device respecting personal data privacy (GDPR compliant).
Making the blockchain world accessible with the tip of a finger. Be the only key! https://www.archethic.net/
Archethic Foundation Non-profit in order to manage decentralized governance of the public blockchain
Do you want to learn more?
White Paper
Yellow Paper
