The First Public Biometric Identity for Universal Authentication

Biometric identity is not new to the world, the first commercial hand geometry recognition systems became available in the early 1970s, arguably the first commercially available biometric device after the early deployments of fingerprinting in the late 1960s.

But until now there is no biometric solution that is for the public or designed for the population of the world. The problems that plague all the current biometric identification are
- Capture and storage of biometric data: Storage of any person's private data has serious privacy concerns. The collection of data could eventually get hacked.
- The biometric data stored in a database may be even more vulnerable than any other data. Passwords can be changed but you can’t change your fingerprint or iris scan. This potentially means that once the biometric data is compromised, it is no longer in your control.
- Your physical identity can be duplicated: For example, a high-resolution photo of your hand from far or copy your fingerprints from a glass you leave at a restaurant. This information could potentially be used to hack you.
- Moreover, storage of the biometric data is useful only for private solutions and not for public and universal authentication. Again the private solutions/networks can be compromised.
- A person who looks similar to you can compromise the security of the biometrics if it runs on facial recognition system or body composition system.
- Most of the biometric solution have a comparison of the measurement with the pattern if the match exceeds a certain threshold then the person is identified.
How is Archethic Biometrics different? Its advantages?
Unlike fingerprints, irises, faces that can easily be reproduced and falsified from a photo on Facebook or in the street - it is impossible to reconstruct the inside of a finger. Archethic Biometrics is based on the internal vein structure of the person's finger and is different for different people and hence is designed for the world population. The device checks vital signs during each authentication to ensure that the finger has not been cut off and that the person is fully aware and consenting, before any transaction validation
Identification by the Archethic biometric device is no longer based on a recognition threshold and therefore no longer needs to be stored for comparison. As shown in the figure below, private cryptographic keys are generated on the fly (and then deleted), allowing the user to retrieve and decrypt their decentralized "key ring". Tolerance on identification is ensured by the learning mechanism described below. Finally, authentication is no longer software, but cryptographic, making any attempt of software attack useless.
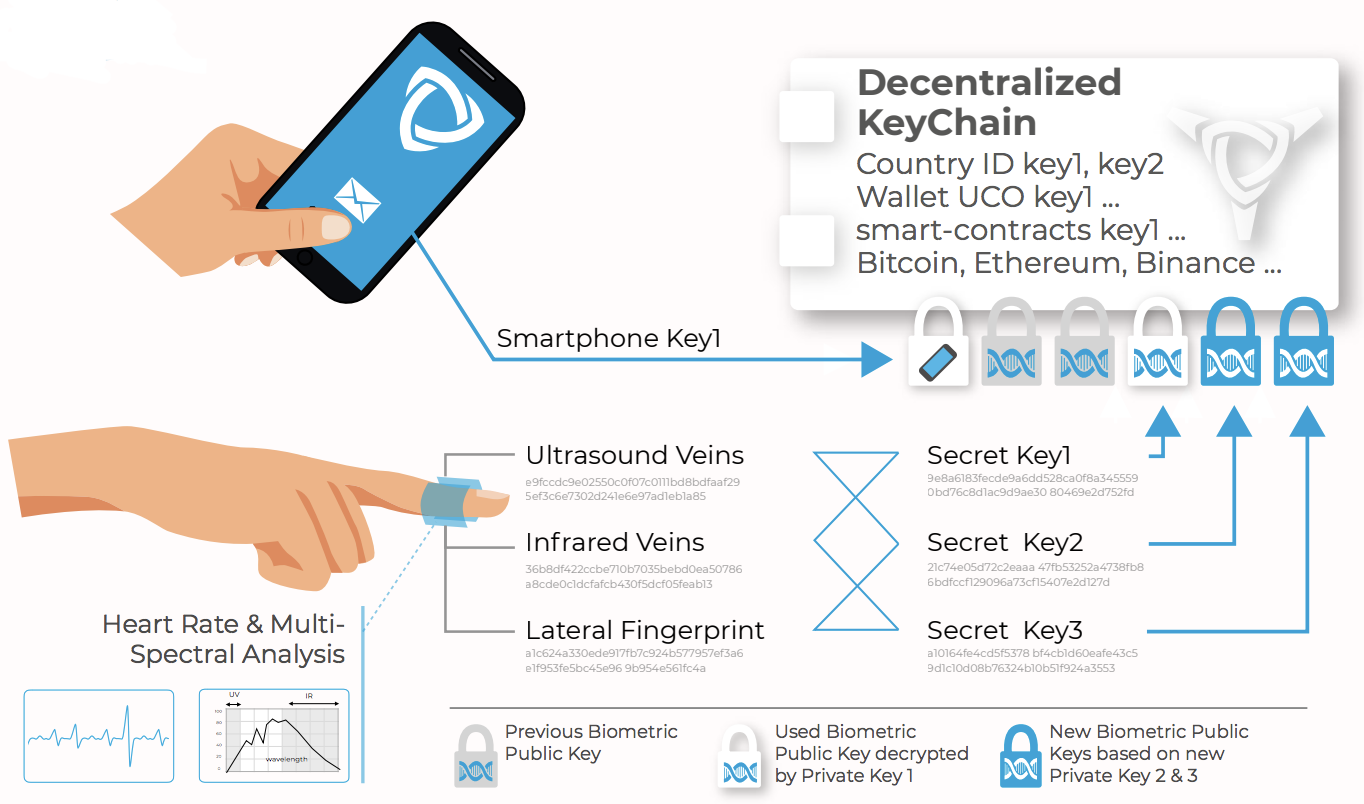
No one will be able to steal your keys, you will be able to delete them, but you will never forget or lose them.
The properties of Archethic Biometrics Device are
- Tamper-proof authentication
- No key storage (GDPR by design)
- Vital signs monitoring
- Learning morphological changes (read below)
- Designed for the world’s population
An authentication Independent of the System
Unlike biometric identification on a smartphone that will only work on one smartphone - Archethic authentication works for any person and on any device. As no keys are stored, it is compatible with the most stringent data protection regulations (GDPR, CNIL, etc.), making biometrics available for large-scale use.
Uniris Biometrics has an Automatic lifelong learning
As shown in the figure above, the keys are generated in pairs from the biometric measurements. If one of the measurements is different (cut, burnt, etc.) then only one key will match and that key can validate the authentication while the two new keys will be added to encrypt (via associated public keys) the decentralized key ring, thus learning a person's new biometric measurements without ever having to store the keys. This also helps in learning morphological changes thereby tracking a person from childhood to adulthood to old age.
Proof of origin of the authentication via Proof-of-work
Identification on the Archethic network is not limited to biometric devices and as shown in the figure above, each access method (smartphone, USB key, software key, etc.) will have its own certification method (read more in the Yellow Paper Season 1). The identification method being associated with the transaction (see smart-contract schema: "OriginKey Sig") and the proof-of-work, will thus allow adjustment of the required security with any smart-contract or portfolio.
For example:
- A transaction of less than 1000 UCO can be carried out from a specific smartphone but only from a biometric device beyond that value.
- Entry into a sensitive building may be made by NFC during the office hours and biometrics outside those hours
There are many biometric solutions that claim themselves as the best. But there is currently no solution that can be used for the world's population, for universal authentication and for the general public except Archethic Biometrics.
Archethic Public Blockchain
Archethic is a Layer 1 aiming to create a new Decentralized Internet.
Its blockchain infrastructure is the most scalable, secure & energy-efficient solution on the market thanks to the implementation of a new consensus: "ARCH".
Archethic smart contracts expand developers' boundaries by introducing internal oracle, time-triggers, editable content & interpreted language.
Through native integration for DeFi, NFTs & decentralized identity; Archethic offers an inclusive and interoperable ecosystem for all blockchains.
In order to achieve the long-term vision of an autonomous network in the hands of the world population, we developed a biometric device respecting personal data privacy (GDPR compliant).
Making the blockchain world accessible with the tip of a finger. Be the only key! https://www.archethic.net/
Archethic Foundation Non-profit in order to manage decentralized governance of the public blockchain
Do you want to learn more?
White Paper
Yellow Paper
